Red Team Pentesting: Understanding What You’re Executing During an Engagement
Juli 21, 2024 - Lesezeit: 3 Minuten
In the realm of cybersecurity, Red Team Pentesting is an advanced approach used to identify and exploit vulnerabilities in systems. While these tests are incredibly valuable for uncovering weaknesses, they also come with their own set of challenges and risks. One crucial aspect of these engagements is understanding precisely what is being executed, especially in terms of the tools and their origins.
Challenges in Red Team Pentesting
Red Team Pentesters employ a wide array of tools and techniques to rigorously test the security measures of a system. While some of these tools are well-documented and widely recognized, others are custom-built for specific scenarios or even created by the testers themselves.
These custom tools and scripts offer significant advantages in terms of flexibility and adaptability, but they also come with risks. Since these tools are often not extensively tested or broadly understood, there is a possibility that they might cause unforeseen problems. For instance, they could lead to system crashes or produce unintended side effects that impact the availability of the target environment.
Another risk associated with using custom or lesser-known tools is the potential for supply chain attacks. If a pentester uses a tool developed or provided by a third party, there is a risk that the tool may contain vulnerabilities or malicious components that go undetected during the engagement.
The Solution: ZeroDetection
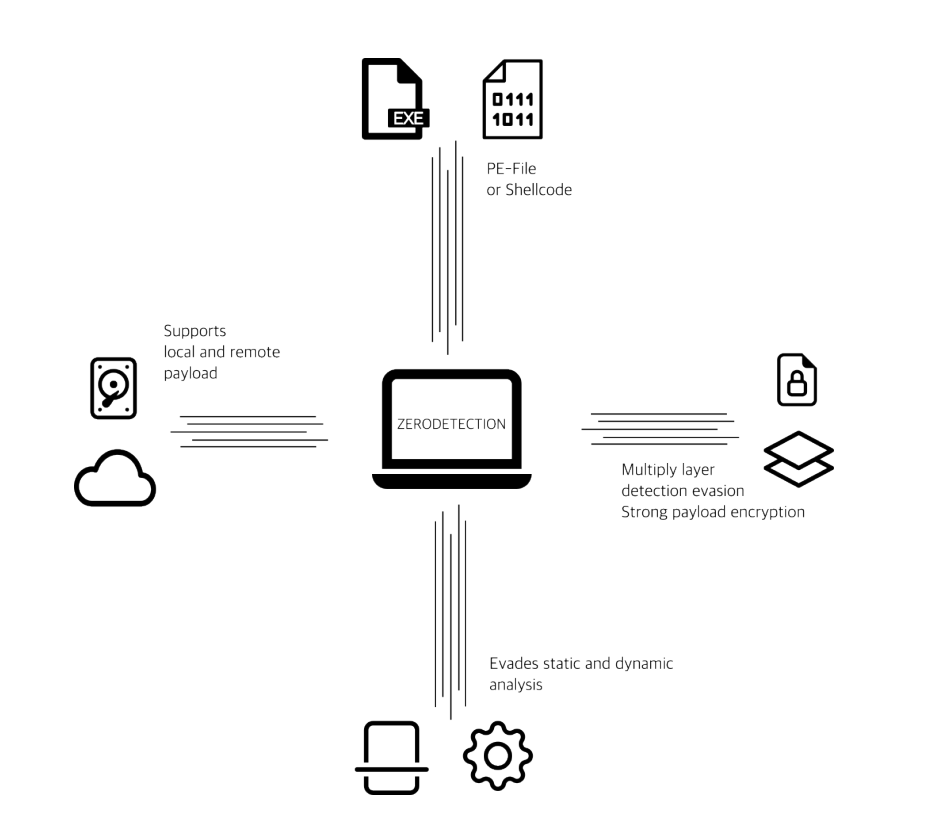
To mitigate the risks associated with using unknown or untested tools, some Red Teams have turned to ZeroDetection. ZeroDetection offers vetted and tested templates specifically designed to minimize security incidents and system crashes during engagements.
ZeroDetection templates are crafted to ensure a high probability of successfully executing an engagement without compromising the target environment. These templates undergo rigorous testing and validation to ensure that they do not introduce unforeseen side effects or additional security risks.
By using such verified templates, Red Team Pentesters can ensure they are employing a controlled and trustworthy method for their tests. This reduces the risk of security incidents and minimizes potential impacts on the availability of the client’s systems.
Conclusion
Red Team Pentesting is an essential tool for enhancing cybersecurity, but it is crucial that the tools and techniques used are well-understood and carefully selected. While custom tools and scripts can be powerful, they also bring specific risks, such as system crashes and supply chain attacks.
Utilizing ZeroDetection or similar vetted and tested templates can significantly reduce these risks. By adopting such technologies, Red Team Pentesters can ensure they perform effective tests without jeopardizing the security and availability of the target environment.