Extract shellcode from memory with x64dbg
April 9, 2024 - Lesezeit: 4 Minuten
In the realm of cybersecurity, understanding how to analyze and extract shellcode from memory is an essential skill for both offensive and defensive purposes. Shellcode, a piece of code typically used in exploiting security vulnerabilities, is often found in the volatile memory of a compromised system. Extracting and analyzing this shellcode can provide critical insights into the methods and intentions of attackers.
One powerful tool for this task is x64dbg, a popular open-source debugger for Windows. In this blog post, we'll explore a step-by-step guide on how to leverage x64dbg to extract shellcode from memory.
Step 1: Set up x64dbg
Firstly, ensure that you have x64dbg installed on your system. You can download it from the official website and install it following the provided instructions. Once installed, launch the x64dbg debugger.
Step 2: Attach to the Target Process
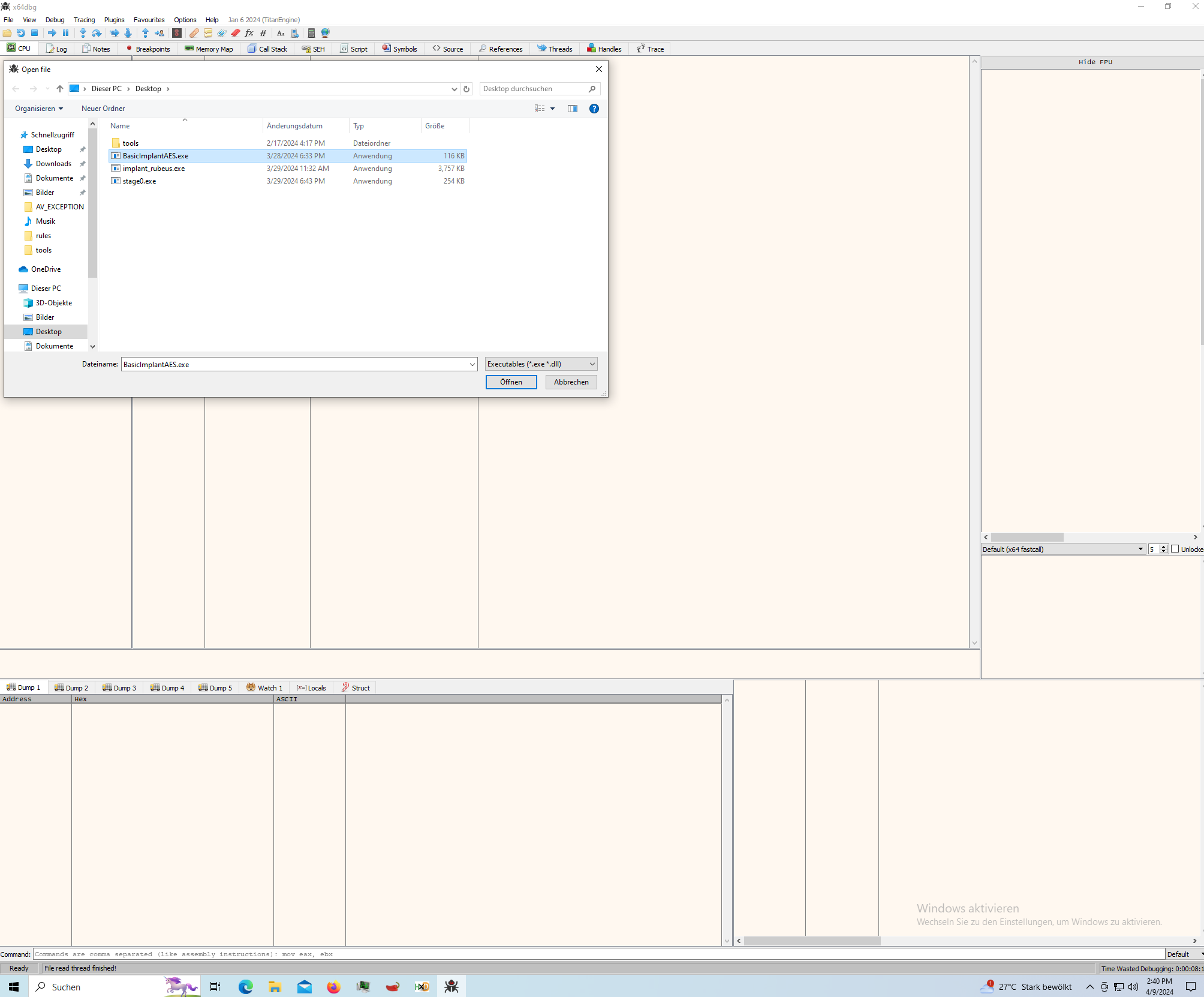
Next, you need to attach x64dbg to the target process from which you want to extract the shellcode. Go to "File" -> "Attach" or open and select the desired process or executeable.
Step 3: Set a Breakpoint on the API Call
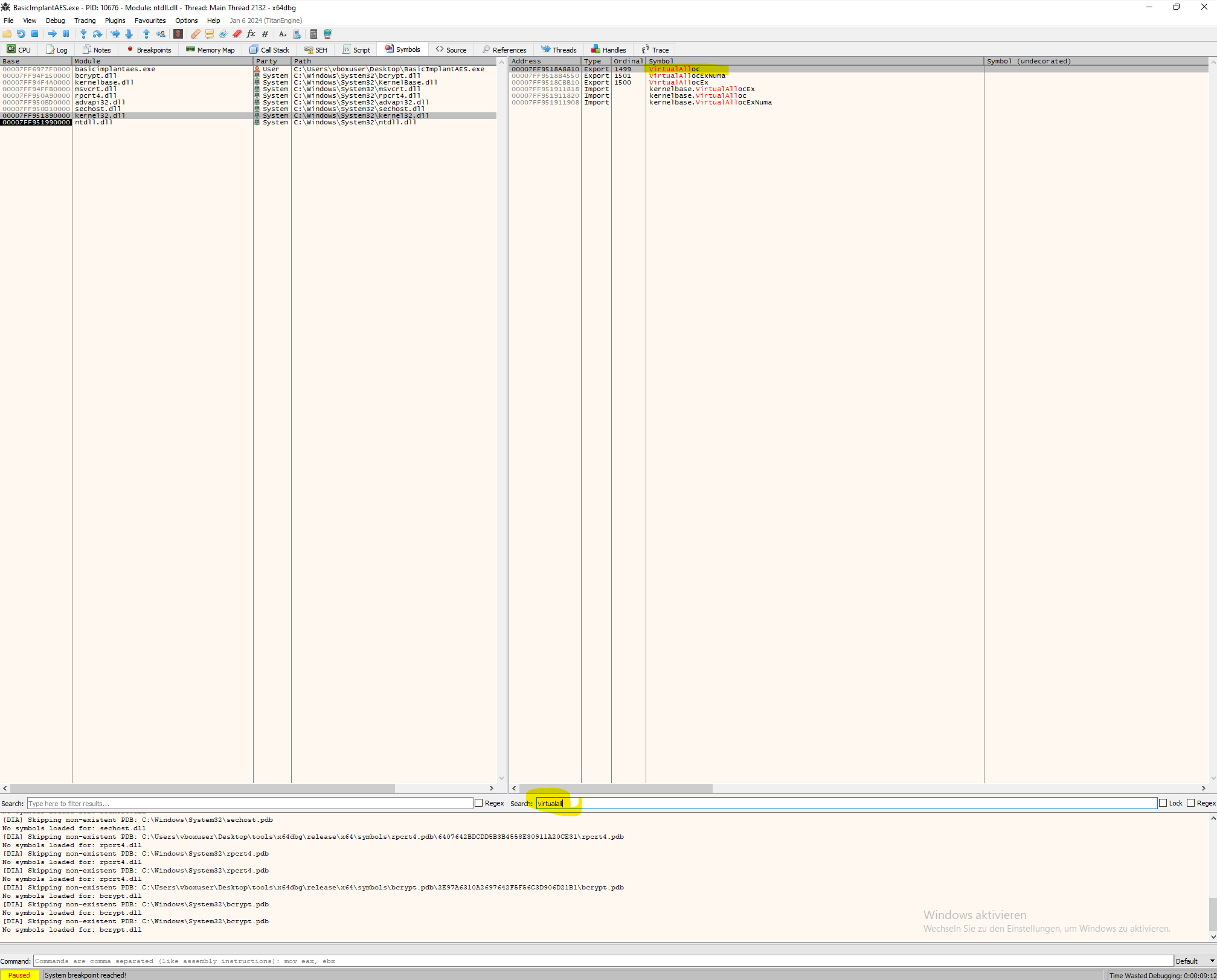
In most scenarios, the Windows API function VirtualAlloc will be used to copy the shellcode into memory. Navigate to the "Symbols" tab in x64dbg and choose kernel32.dll. Type "VirtualAlloc" in the search bar and select it. Press F2 or right-click and select "Toggle Breakpoint" to set a breakpoint on VirtualAlloc. Then, go to the "Breakpoints" tab and delete all breakpoints except the VirtualAlloc breakpoint.
Step 4: Get the Memory Address from the Register
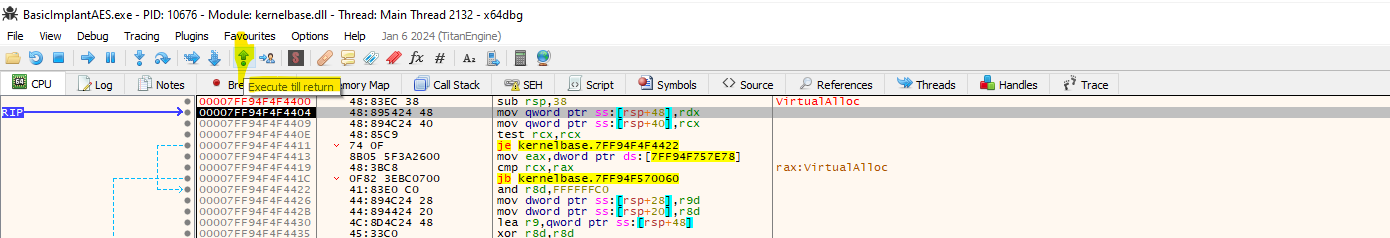
Press "Run", and the execution should stop at the breakpoint set on VirtualAlloc. Press "Execute till Return", and double-click on the EAX or RAX register. In the Dump Window, you should see a blank memory region. Press "Execute till Return" again, and now the shellcode should appear.
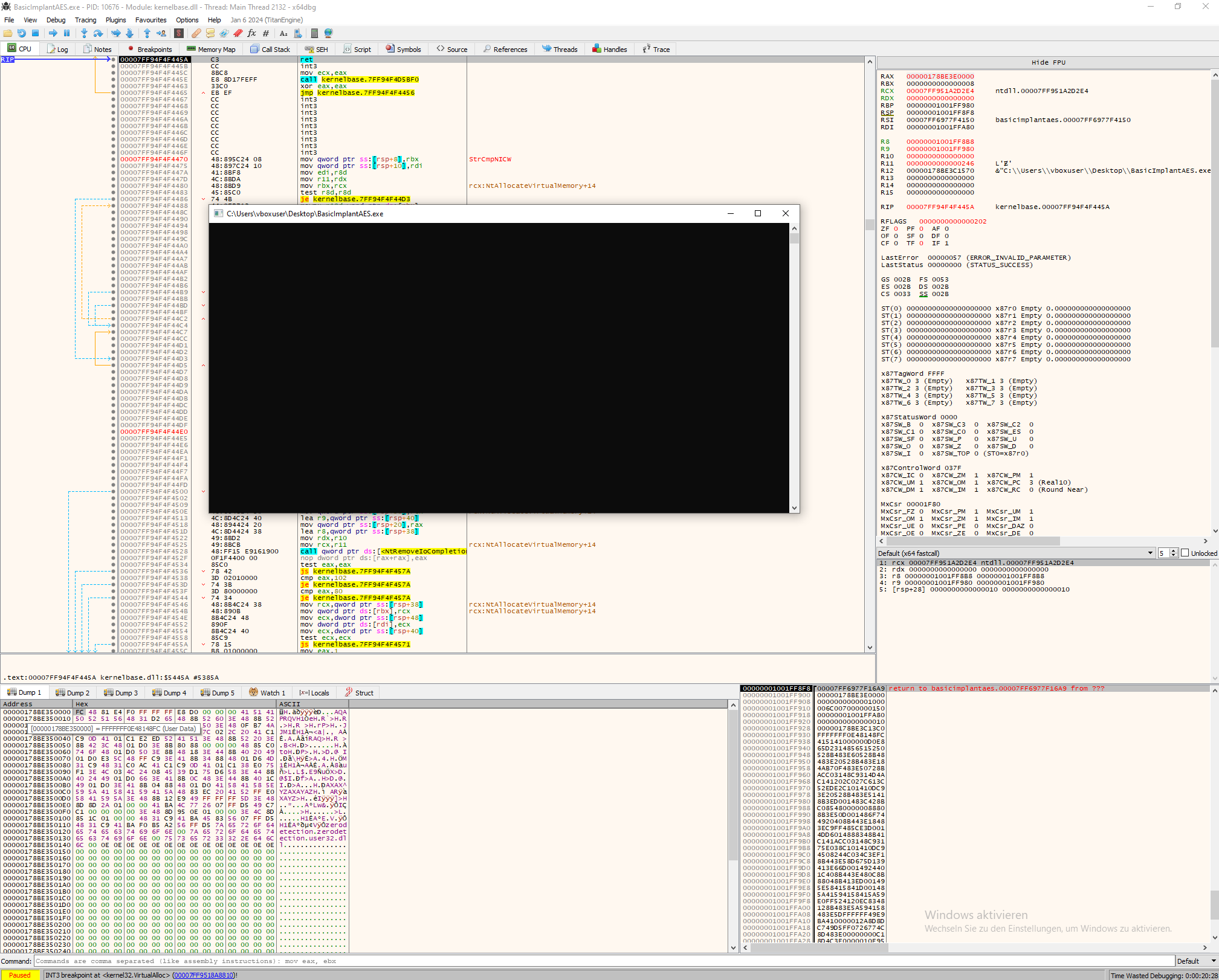
Even our sample malware uses AES-encrypted payload. During execution, these payload will be decrypted. The upside is that we can decrypt the shellcode and extract it in cleartext.
Conclusion
Extracting shellcode from memory is a crucial aspect of malware analysis and cybersecurity research. With the right tools and techniques, such as x64dbg, analysts can effectively extract and analyze shellcode to gain insights into the tactics and techniques employed by adversaries. By understanding how to extract shellcode from memory, security professionals can better protect systems and networks from potential threats.